Knowledge Centre
1. Title of Subcategory
A qualification gets you in the door. A designation keeps you in the game — and makes sure people pay you what you’re worth.
2. Explainer Video (top of page)
1–3 min video from a staff member or subject expert explaining:
What the topic is
Why members should care
How it connects to their work, compliance, or earning power
3. What You Need to Know
Cybersecurity is the practice of protecting computers, networks, servers, mobile devices, and data from digital attacks, theft, or damage. Cybersecurity is like locking the doors and windows of your digital world, it keeps hackers and viruses from getting in and stealing or destroying your information.
4. Why It Matters to You (Impact section)
We use technology for almost everything- banking, communication, business, and education. Without cybersecurity, criminals could:
Steal personal or business data
Commit fraud (e.g., using stolen credit card info)
Spread harmful software (malware or viruses)
Disrupt systems and cause data loss
5. Types of Cybersecurity
Network Security: Protects the network (like Wi-Fi or company systems) from hackers.
Information Security: Keeps data private and safe from unauthorized access.
Application Security: Ensures software and apps are built safely.
Cloud Security: Protects data stored on cloud platforms (like Google Drive or OneDrive).
User Awareness: Training people to recognize scams, phishing emails, and unsafe links.
Common Threats
Phishing: Fake emails or messages that trick you into giving personal info.
Malware: Software designed to damage or spy on your computer.
Ransomware: A hacker locks your data and demands money to release it.
Data Breaches: When private information is leaked or stolen.
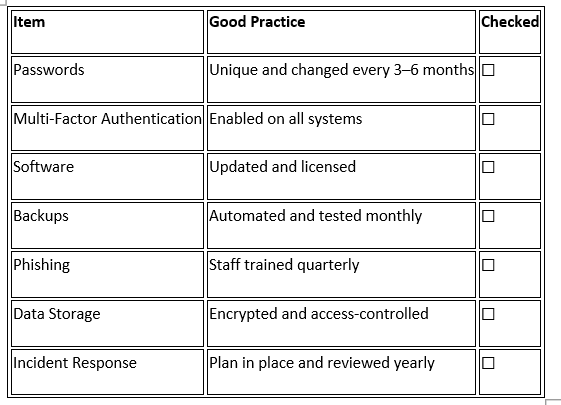
Good Cybersecurity Habits
Use strong passwords (mix of letters, numbers, symbols).
Update software regularly.
Don’t click suspicious links or attachments.
Use antivirus software and firewalls.
Back up important files regularly.
6. How to Apply (Action steps)
6.1. When a Client’s Email Is Hacked
A client’s compromised email can expose confidential financial data. Immediate and coordinated action helps limit damage.
Immediate Actions:
1. Alert the client immediately via phone or SMS.
2. Stop all pending financial transactions.
3. Change all passwords (email, portals, bank).
4. Enable two-factor authentication (2FA).
5. Scan all devices for malware.
6. Verify recent communications for tampering.
7. Report the breach under POPIA if necessary.
6.2 How to Secure PDF Financials
Accountants must protect financial documents before sharing.
- Password-protect all PDFs.
- Apply restrictions (no copy/edit/print).
- Digitally sign documents.
- Share via encrypted or password-protected channels.
- Verify recipient addresses.
- Store securely in encrypted folders.
6.3 Preventative Measures for Accounting Firms
- Conduct annual cybersecurity awareness training.
- Use multi-layered security (firewall, antivirus, VPN).
- Regular encrypted backups.
- Maintain a Cyber Incident Response Plan.
- Align with POPIA, IFAC Code of Ethics, and CIBA standards.
6.4 Red Flags to Watch For
⚠ Urgent payment requests with new bank details – possible fraud.
⚠ Poor grammar or tone – impersonation.
⚠ ‘Invoice overdue’ emails – phishing.
⚠ Unexpected password reset emails – breach risk.
6.5 Quick Reference Checklist
☑ Client informed & communications verified
☑ Passwords reset & 2FA enabled
☑ Device scans completed
☑ Incident logged internally
☑ PDF files secured
☑ Data shared securely
☑ Backup verified
7. Common Cybersecurity Mistakes Accountants Should Avoid
Accountants handle highly confidential information including financial data, payroll details, ID numbers, tax files, and client records. This makes them prime targets for cybercriminals. A single careless click or weak password can lead to data breaches, regulatory penalties, or loss of client trust.
Below are the most common cybersecurity mistakes accountants must be aware of; and how to prevent them.
7.1 Using Weak or Reused Passwords
Problem:
Many accountants reuse simple passwords across multiple systems (e.g., “12345,” “Password2025,” or birthdays). Hackers use automated tools to guess these quickly.
Example:
A hacker accesses a firm’s cloud accounting portal using a reused password from a leaked social media account.
Solution:
Use strong, unique passwords (mix of uppercase, lowercase, numbers, and symbols).
Enable multi-factor authentication (MFA) on all systems (e.g., Xero, QuickBooks, SARS eFiling).
Use a password manager for secure storage.
7.2 Falling for Phishing Emails
Problem:
Cybercriminals often impersonate SARS, banks, or senior partners to trick staff into clicking malicious links or sharing credentials.
Example:
An email says: “SARS refund pending - click to verify.” Clicking the link installs malware that steals client data.
Solution:
Always verify sender email addresses carefully.
Don’t click on suspicious links or attachments.
Train all staff on phishing awareness through CPD or internal sessions.
7.3 Ignoring Software Updates
Problem:
Failing to update software or antivirus tools leaves systems exposed to known vulnerabilities.
Example:
A firm still uses an old version of Windows or outdated antivirus, making it easy for ransomware to infect the system.
Solution:
Turn on automatic updates for operating systems and accounting software.
Keep firewalls and antivirus software active and up to date.
7.4 Using Public Wi-Fi for Work
Problem:
Public Wi-Fi (e.g., in coffee shops or airports) can be intercepted by hackers.
Example:
An accountant sends a client’s payroll file via email using hotel Wi-Fi. The hacker captures the data.
Solution:
Avoid using public Wi-Fi for sensitive work.
If unavoidable, use a VPN (Virtual Private Network) for encryption.
7.5 Poor Data Backup Practices
Problem:
Some firms rely on one local backup or none at all. If data is lost or encrypted by ransomware, recovery becomes impossible.
Solution:
Use cloud-based backups (encrypted and automatic).
Keep at least two backup copies (one offline, one cloud).
Test recovery regularly.
7.6 Sharing Confidential Information via Unsecured Channels
Problem:
Sending tax files, ID copies, or payslips through normal email without encryption exposes sensitive data.
Solution:
Use encrypted email services or secure client portals.
Protect attachments with passwords or encrypted ZIP files.
7.7 Neglecting Employee Training
Problem:
Staff are often the weakest link — they may not recognise phishing, social engineering, or suspicious attachments.
Solution:
Conduct regular cybersecurity awareness sessions.
Establish a simple “report suspicious email” procedure.
Include cybersecurity in onboarding and CPD programmes.
7.8 Not Restricting Access Rights
Problem:
All employees have full access to client data or financial systems, even when unnecessary.
Example:
An intern accidentally deletes client folders because access was unrestricted.
Solution:
Apply the principle of least privilege: give access only to what’s needed.
Review access levels quarterly.
7.9 Ignoring Device Security
Problem:
Unprotected laptops, USB drives, or phones create risks if stolen or infected.
Solution:
Enable passwords and screen locks on all devices.
Use encryption for sensitive files.
Avoid using personal USB drives on office computers.
7.10 Failing to Report or Respond to Incidents Quickly
Problem:
Some firms try to “handle it quietly” or delay reporting a breach, worsening damage.
Solution:
Have a Cyber Incident Response Plan (who to call, what to do, how to notify clients).
Report major breaches to the Information Regulator under POPIA.
Learn from every incident to prevent recurrence.
8. Related Resources